A Tutorial for Ubuntu 9.04
About a month ago, I wrote an introduction to using the Dropbox service to backup your important data. Any data that you backup with Dropbox is encrypted and uploaded to Amazon’s S3 service. Unfortunately, it is the people who run Dropbox that hold the keys used to perform this encryption. Regardless of how great the service is, storing your files with Dropbox involves placing your trust in the people who currently run the Dropbox service, as well as all of the people who will ever run Dropbox in the future. This is an unacceptable risk for many people and many kinds of data.
Thankfully, there is a strategy that can greatly reduce the risk. It is possible to automatically encrypt your files, and then use Dropbox to backup the encrypted versions. This means that you can have your cake and eat it too! Dropbox provides a convenient backup strategy so that your files can’t be lost due to the theft or destruction of your laptop. The encryption software ensures that your files can’t be accessed by anyone who works for Dropbox, or any hackers that might have infiltrated the servers that Dropbox uses.
If you’re using Ubuntu, the software that you need is free, and it isn’t especially difficult to set up. Please note that this tutorial will require you to use the command-line and edit some configuration files. Don’t be afraid! I will try to explain the process in a step-by-step fashion. If you’re just getting started with Linux, this project might help you get used to the command-line a little bit.
(Note: this has been tested on Ubuntu 9.04 only; I am not confident that these exact instructions will work on older versions of Ubuntu.)
Part 1: Set Up Dropbox
The rest of this tutorial will assume that you have the Dropbox client software installed on your computer. Detailed instructions can be found in the “Installing Dropbox” section of my previous post on the Dropbox service. When you have finished following those instructions, proceed with Part 2.
Part 2: Removing Unencrypted Data
This section only applies if you have already used Dropbox to store some data that you would now like to encrypt. If you have never stored any files in your Dropbox, skip ahead to Part 3.
The first step is to take all of the contents of your Dropbox folder and back them up somewhere else. The following command will copy everything in your Dropbox into a folder named “DropboxBackup” (open a Terminal by clicking Applications -> Accessories -> Terminal):
cp -r ~/Dropbox ~/DropboxBackup
Once everything has finished copying, it might even be a good idea to burn this folder to a CD, just to be safe. Now we can proceed to delete all of the files in the Dropbox folder. Open your Dropbox folder in the file manager by left-clicking on the Dropbox applet in the top-right. Click the “View” menu and ensure that “Show Hidden Files” is checked. Next, select all the files and hit the Delete key. Dropbox should begin synchronizing the changes. Unfortunately, once the synchronization completes, nothing will have been actually deleted yet; the files will simply be marked as deleted, but it will still be possible to recover them.
In order to actually get rid of the files, open your web browser, go to www.getdropbox.com and log in. Click the “Show deleted files” button.
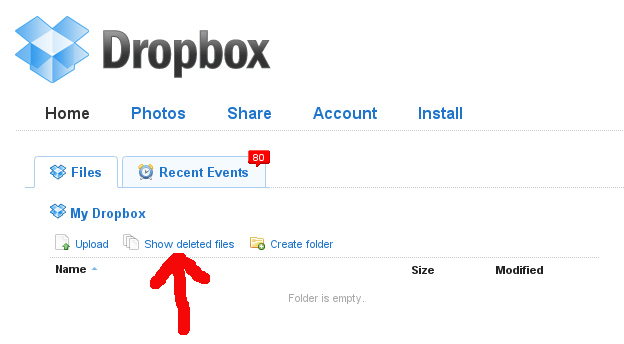
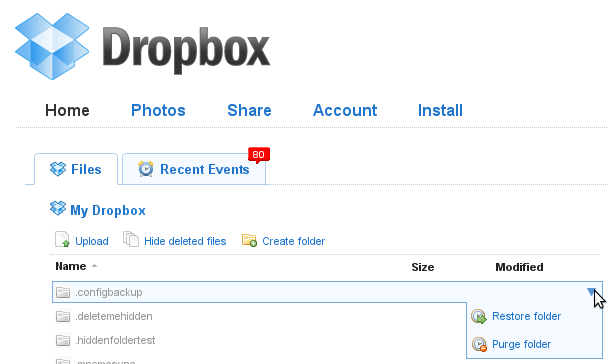
For each deleted file, select the “Purge” option.
Part 3: Reconfiguring the Dropbox Client
The encryption software that will allow you to secure your Dropbox is called “EncFS“. It works by creating a folder in which to store an encrypted version of each of your files and folders, and then making the unencrypted names and content available in a different folder. When we are finished with this tutorial, the folder containing the encrypted files will be stored within the Dropbox folder, and will therefore be automatically backed-up. Since we don’t want to accidentally store any non-encrypted files in the Dropbox folder, we will move the real Dropbox folder to a hidden location.
Right-click on the Dropbox applet and choose “Preferences…”; under the “Main” tab, click “Move…”:

Move to your Home Folder and click the “Create Folder” button. Give the new folder the name “.dropbox_encrypted” and click “Open”. Close the preferences window. On to Part 4!
Part 4: Configure an Encrypted Filesystem with EncFS
Now we’re ready to actually do some encrypting. In the commands that follow, you will need to substitute your username in place of <<yourusername>>. Open a terminal and enter these commands:
sudo apt-get install encfs libpam-mount sudo adduser <<yourusername>> fuse
(As an example, if your username is “pragmattica”, then the command just above should be sudo adduser pragmattica fuse)
Now you need to log out and log back in again before continuing. Next, run this command:
encfs ~/.dropbox_encrypted/Dropbox/encrypted ~/Dropbox
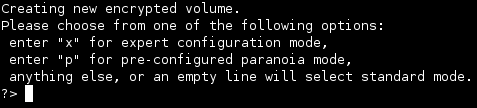
The encryption software will ask you a series of questions. Enter the following responses:
- Enter ‘y’ to create the encrypted directory
- Enter ‘y’ to create the unencrypted directory
- Enter ‘x’ to choose expert Mode (I experimented with the pre-configured paranoia mode, but encountered performance issues)
- Enter ‘1’ to use the AES cipher algorithm
- Enter ‘256’ for the key size
- Enter ‘1024’ for the block size
- Enter ‘1’ for block filename encoding
- Enter ‘y’ for filename initialization vector chaining
- Enter ‘n’ for per-file initialization vectors
- Enter ‘n’ for block authentication code headers
- Enter ‘y’ for file-hole pass-through
- Enter and repeat the password for the new encrypted filesystem; in order for the next part of the tutorial to work, the password must be the exact same password that you use to log in to your computer after turning it on
I’m probably not telling you anything that you don’t already know, so I’ll be brief. A good password should consist of upper and lower-case letters, numbers and punctuation characters. It should be fairly random looking, and pretty long; more than 20 characters, preferably.
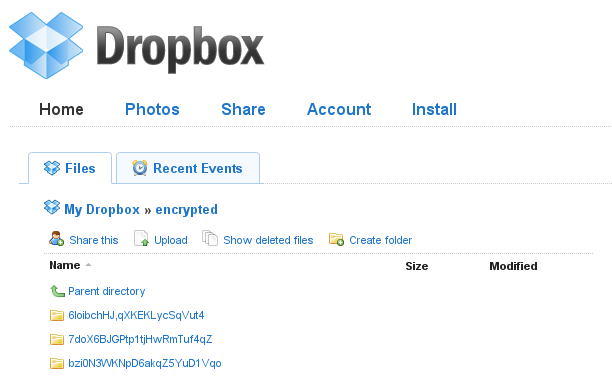
You can now begin copying files into your /home/<<yourusername>>/Dropbox directory. The files that you copy in should be encrypted and backed-up by Dropbox. If you log in to the Dropbox website, all of the saved files should have meaningless gibberish names and encrypted contents.
Part 5: Use pam_mount to Automatically Mount Your Encrypted Filesystem
At this point, it would be possible to use the command-line to manually mount your encrypted filesystem every time you turn your computer on, but we can do better. A program named “pam_mount” can automatically mount the filesystem as soon as you log in. Open a terminal and enter this command:
sudo gedit /etc/security/pam_mount.conf.xml
Look for the line:
<!-- Volume definitions -->
Right beneath that line, add this new line:
<volume user="<<yourusername>>" fstype="fuse" path="encfs#/home/<<yourusername>>/.dropbox_encrypted/Dropbox/encrypted" mountpoint="/home/<<yourusername>>/Dropbox" />
To eliminate a harmless but annoying error message, use “sudo gedit” as above to edit the /etc/pam.d/common-pammount and /etc/pam.d/common-auth files and eliminate all occurrances of the word use_first_pass.
The next time you turn your computer on and log in, you should be able to go to your new /home/<<yourusername>>/Dropbox folder and see the unencrypted versions of your important files. Unfortunately, this new folder won’t display the little status icons on each file, so you’ll have to keep an eye on the Dropbox applet to know when the synchronization of your files is in progress or complete. I think that this is a very reasonable sacrifice for the additional security.
One last tip: the icon for your secure Dropbox folder is now the same as for every other folder. To give that folder some visual distinction, it’s possible to change its icon. Right-click on the folder and select “Properties”. Click on the little Folder icon in the top-left of the properties dialog box and set the icon to /usr/share/icons/hicolor/64×64/apps/dropbox.png.
![]()
Security Considerations
As an added benefit, this strategy will also provide a little protection against your information being compromised by someone who steals your laptop. The reason this only provides a little protection is due to the tendency of modern operating systems and software to scatter bits of information about while working. The actual files themselves are encrypted, but unencrypted bits of the files might still end up lying around in temporary files or the swap partition. An attacker with enough skill and determination would be able to find those. Still, it’s better than nothing.
This is probably going to be my last security-related post for a while. I’ve been going through a security phase lately, but I’m feeling pretty good about the precautions that I now have in place. Next post, I will be back to my regularly scheduled programming topics. As always, if you have any problems with anything in the tutorial, just leave a comment. I’m always happy to help.
How would you handle multi-machine syncing as this example seems to assume only one machine syncing with Dropbox. I have 4 machines that sync to the same account and would like to know how to handle that scenario.
Comment by Spence — May 11, 2009 @ 4:02 am
@Spence: That is an excellent question! You’re completely correct that I haven’t really talked about multiple machines. The good news is: if your other machines are also Ubuntu 9.04, then it should be easy to set up sharing. You would need to install Dropbox on your second Ubuntu box, link it to your account, and move the location of the Dropbox folder as described in “Part 3”. You would then be able to create an empty “~/Dropbox” folder and mount your EncFS filesystem with “encfs ~/.dropbox_encrypted/Dropbox/encrypted ~/Dropbox”. You could then also set up pam_mount to do the mounting step automatically, as described in “Part 5”. From the Wikipedia, it seems that EncFS also supports FreeBSD and Mac OS X, so it would also be possible to set up for these systems, though unfortunately I don’t have specific instructions. Unfortunately, EncFS doesn’t seem to support Windows at all, so if one of your machines runs Windows, then you may be out of luck with this particular encryption software. Sorry about that! Can you give some more details about the computers you use?
Comment by bnsmith — May 11, 2009 @ 8:36 am
I actually have 1 – Jaunty, 2 – Intrepid and 2 – Hardy machines. So looks like I’ll need to do some further research and testing to see if I can get this to work seamlessly. I’d really like to have the encryption since 1 machine is a netbook and 1 machine is a notebook that travel with me often.
Comment by Spence — May 16, 2009 @ 8:42 pm
Hi! Same problem with me too… Mixed ubuntu versions and architectures 32-64 bits. Different EncFs versions were installed on different systems so I’ve tried to compile the 1.4.2-2 (jaunty’s default build for now) on a 8.04 as a start but without success. But is a solution to stabilize a common EncFs version between systems? If anyone figures out this please reply… Thanks.
Comment by Ch Iossif — May 17, 2009 @ 5:56 am
My understanding is that one of the main problems with multiple Ubuntu versions is not actually EncFS, but pam_mount. Apparently there were some bugs in that package in earlier releases. I have an older Ubuntu box (Heron, I think) that I’ve been meaning to get up and running with Dropbox. I’ll let you know what I find.
Comment by bnsmith — May 17, 2009 @ 3:34 pm
I’ve made some progress on my Hardy Heron box. This box was upgraded to Hardy, no fresh install. It has also seen a lot of use and fiddling, so no guarantee that this will work for you, but these are the steps I’ve followed:
* In terminal: sudo gedit /etc/apt/sources.list
* Edit the file and change ‘hardy’ to ‘jaunty’
* In terminal: sudo apt-get update
* In terminal: sudo apt-get install encfs
* In terminal: sudo gedit /etc/apt/sources.list
* Edit the file and change ‘jaunty’ back to ‘hardy’
* In terminal: sudo apt-get update
* In terminal: sudo adduser yourusername fuse
* Then log out and back in
* In terminal: mkdir ~/visible
* In terminal: encfs ~/path/to/encrypted ~/visible
This should at least let you see your encrypted files. After that, all you need is pam_mount to do it automatically on login, which I haven’t set up yet, so I can’t comment on how hard that would be.
Comment by bnsmith — May 17, 2009 @ 8:32 pm
Thanks. It has worked. Here is an edited copy from my terminal history /**/ :
sudo apt-get update
sudo apt-get upgrade /* Everything was updated – No error or warning occured */
sudo cp /etc/apt/sources.list /etc/apt/sources.list.hardy /* this is not a file for experiments ! backup */
sudo gedit /etc/apt/sources.list /* and here I’ve replaced all hardy with jaunty */
sudo apt-get update /* Can I use this trick for a version upgrade? 🙂 THIS IS A JOKE… */
sudo apt-get install encfs /* YES, YES… */
sudo mv /etc/apt/sources.list.hardy /etc/apt/sources.list /* Ouff, ouff … */
sudo apt-get update
sudo apt-get upgrade /* No more news – Everything is ok. */
mkdir -p private_Dropbox
mkdir -p /Dropbox/private /* Dropbox installed and up to date */
gedit .bashrc /* comment A */
source .bashrc
dropboxmount_private /* mounting the private */
cd private_Dropbox
cat /* YES the contents are available */
cp ../.bashrc . /* put a new to see */
dropboxumount_private /* unmounting */
/* comment A:
Here I typed the following aliases as seen from another forum:
alias dropboxmount_private=’encfs ~/Dropbox/private ~/private_Dropbox’
alias dropboxumount_private=’fusermount -u ~/private_Dropbox’
I prefer not to use pam_mount just the previous alias procedure
*/
With the previous lines I’ve seen correctly the authentically jaunty encrypted files and I’ve put a new one for test. The last one will be tested in 8 hours – on problem I’ll be back… it is my home pc.
Finally: it worked, but IMHO this is not the correct solution.
Each ubuntu multi-version user HAS TO PAY ATTENTION on EncFs available version for his installations. And what will happen after an encfs update? I’ll use it only for a limited time period file transfering.
Thanks a lot.
Comment by Ch Iossif — May 18, 2009 @ 1:52 am
I finally went ahead and set up pam_mount on my Hardy Heron box. I followed the same basic steps as I did to get the latest version of encfs. I do feel a little less confident about the safety of the following method, because it involves updating an important package, so use it at your own risk.
* In terminal: sudo gedit /etc/apt/sources.list
* Edit the file and change ‘hardy’ to ‘jaunty’
* In terminal: sudo apt-get update
* In terminal: sudo apt-get install libpam-mount
* In terminal: sudo gedit /etc/apt/sources.list
* Edit the file and change ‘jaunty’ back to ‘hardy’
* In terminal: sudo apt-get update
* Set up pam_mount as described in the post
Comment by bnsmith — June 8, 2009 @ 6:33 pm
Dropbox sounds great but it lacks some important features for me, since I mostly backup external HDD, network drives and USB drives from both my Pc and Mac. Most providers don’t have these features but this wasn’t a problem for SafeCopy (www.safecopybackup.com). It allows me to do the above features plus I can share the same account for both my Mac and Pc. I’m very happy with it and it’s worth checking out.
Comment by Dobi — May 12, 2009 @ 8:52 am
Hey, great article. Really easy to follow and provides a great added value to dropbox. I have just one question. When I encrypted the folder, I ended with file on the unencrypted dropbox folder (~/.dropbox_encrypted/Dropbox/) named .encfs6.xml.
Does this means a security hole? Is it ok to leave that file there, or should I remove it?
Thanks for the help.
Comment by Ricardo — May 16, 2009 @ 7:44 pm
@Ricardo: DO NOT DELETE THAT FILE! That file is metadata about the encrypted filesystem itself. According to a mailing list thread that I found, if you delete that file, you can’t unencrypt any of your files. See the thread here:
http://sourceforge.net/mailarchive/forum.php?thread_name=4803FE11.305%40sidvind.com&forum_name=encfs-users
As long as your password is kept safe, other information about the encrypted filesystem (such as which program you used, or even the full source-code of that program) shouldn’t really help any potential attacker that much.
Comment by bnsmith — May 16, 2009 @ 8:12 pm
How do you decrypt on a new computer using your .encfs6.xml from the Dropbox encrypted folder on the old computer? What are the steps to do this just in case I crash my current linux box?
Comment by DecryptorQuestion — April 22, 2010 @ 7:39 pm
@Dobi: I looked at SafeCopy, and it seems to have some advantages. Their paid program gives more GB for less money. Unfortunately, their Linux version is only in Beta right now, and they don’t offer any free service. Only a 1 GB trial for 7 days.
Comment by bnsmith — May 16, 2009 @ 8:18 pm
@bnsmith: thanks a lot for the feedback!! 😀
Comment by Ricardo — May 17, 2009 @ 3:19 am
It’s perfect service. We share all our files between or team on all projects!
Comment by Dropbox — June 16, 2009 @ 4:58 am
Well, it’s now a few months later and all my machines are on Jaunty (32, 64 & LPIA). I’ve got one machine syncing and will add the rest shortly. However, should I need to do a restore of a single file, how might that be accomplished? Also, if I need to pull a file from my online Dropbox to another machine via the web interface, how would that be accomplished? I’m guessing that neither are possible, but I just have to ask.
Comment by Spence — August 14, 2009 @ 11:44 pm
I did some reading on this, and without the metadata information included in the .encfs6.xml file, it is impossible to decrypt ANY of the files. If you wanted to decrypt a single file, you would at least need to have a directory with that file, and then the encrypted file that you wanted, with all of the proper directory structure. I haven’t played with this much myself, but I think it might be possible to mount something set up like that, and then you could get at the file. However, since the filename is encrypted, you wouldn’t know which file to download from Dropbox 🙂
There is a debug utility that you can use on the command-line to get the decrypted filenames of files, and possibly decrypt them as well, so the situation isn’t hopeless. It would probably just take a lot of playing around to figure this stuff out. If you do invest the time and figure some of this out, maybe write a post about it on your blog and link to it here.
Comment by bnsmith — August 15, 2009 @ 7:29 pm
How do you decrypt your encrypted Dropbox data onto a machine that has never had any of this installed?
Comment by DecryptorQuestion — April 22, 2010 @ 7:12 pm
Just to add to my post… When you sync multiple machines to the same account, you will need to use the .encfs6.xml from the first machine you sync to Dropbox on all other machines. Just follow the same directions, the files will sync but not be visable in your Dropbox folder. After the sync is complete on the other machines, you’ll need to either remount the encfs folder or just reboot. When syncing, the unique .encfs6.xml on the other machines will be marked as conflicts, just leave them or move them.
Comment by Spence — August 18, 2009 @ 1:07 pm
DropBox is great and so is your solution (of course with its limitations). But it is extremely inconvenient and time consuming for everyone to be using this or any other way of encrypting their data. I just hope those guys @ DropBox take care of this at their end.
Comment by Rahul J — September 6, 2009 @ 4:21 pm
I’d be a little worried about the Dropbox folks writing the software that handles this for us. That would again be putting our trust in them, just as we do if we don’t encrypt. I’d feel safer if they had an API that would allow us to use any one of a number of open-source encryption programs; whichever one we prefer and trust the most.
Comment by bnsmith — September 14, 2009 @ 2:31 pm
This is a great idea – have you tried suggesting this to them? They seem open to cool new ideas like this.
Also, it’d be another way for them to add value to their paid offerings, if they so chose.
Comment by Alain — October 21, 2009 @ 1:21 pm
@Alain: I think that they’ve been talking about adding that feature for a while now. I guess they’re just swamped trying to scale up to demand and haven’t had time.
Comment by bnsmith — October 21, 2009 @ 1:44 pm
It’s a cool tutorial, but spideroak does all of this automatically from the client side, including handling multiple machines. It’s all zero-knowledge, and no one but you can decrypt the data.
Comment by ax0n — October 21, 2009 @ 1:06 pm
That spideroak site is pretty neat. What a weird name though…
Anyway, I haven’t actually downloaded their client yet, but I imagine that they’ll have to have worked pretty hard to match the ease-of-use that Dropbox has. I’ll have to give it a try.
Comment by bnsmith — October 21, 2009 @ 1:43 pm
There is a much simpler solution for encrypting dropbox files with box windows/linux. Truecrypt. Create a encrypted volume and assign a secure passphrase. Install truecrypt on any pc you need to access dropbox or even upload the Truecrypt standalone client. just mount the truecrypt volume as any drive. Done.
Comment by COdy — October 21, 2009 @ 2:55 pm
That’s a good thought. In fact, that was actually my first thought in how to make this work. Unfortunately, whenever the truecrypt file is mounted, the file is locked and Dropbox won’t synchronize it. So if you mount your truecrypt volume when you’re logged in, and then unmount it when you log out (automatically), then there won’t be any time available when Dropbox can sync it.
Comment by bnsmith — October 21, 2009 @ 3:02 pm
bnsmith,
Dropbox doesn’t sync? I have never had an issue with it not syncing, I mount the volume directly from the Dropbox folder and any changes always sync back up to the server.
Comment by COdy — October 21, 2009 @ 8:47 pm
It’s possible that things have changed since I first tried it months ago. So are you saying that if you mount the Truecrypt volume, and then put some files in it while mounted, Dropbox will sync the volume even while it’s still mounted? You don’t have to unmount first to start the syncing? If that’s true, then perhaps that might be a workable option.
Comment by bnsmith — October 22, 2009 @ 8:05 am
I will confirm this in the mourning. As far as I know, when you make a change to the encrypted volume it has changed and dropbox starts syncing the changed file from the local dropbox folder backup to the dropbox server.
The one part of your question I don’t understand is the login/logout with no time to sync? Are you referring to the dropbox webpage or disable the desktop client?
Cody
Comment by Cody — October 23, 2009 @ 12:40 am
@Cody: If you set up PAM mount to automatically mount the TC volume when you log in, and then automatically unmount it when you log out, then that means that the TC volume is mounted whenever you are logged in. The Dropbox client is also only running whenever you are logged in. So if Dropbox won’t sync a mounted TC volume, then there’s no time for syncing to take place, since the volume is mounted during the whole time that the Dropbox client is running. That was what happened to me, anyway. Either Dropbox or TC may have made some change that fixes this problem in the intervening months.
Comment by bnsmith — October 23, 2009 @ 7:20 am
yea, I see what you are saying. I do not automount my TC volumes as they are sensitive files that I would not want someone to access without a secure pass-phrase. When I unmount the TC volume dropbox syncs just the changes to the single volume and not the entire volume so it works perfectly for me.
Comment by COdy — October 27, 2009 @ 8:44 am
I was planning to do this. Now I can just follow your howto. This is the reason why howto writers go to heaven O:).
Anyway I prefer having an encrypted directory inside DB to have sensitive data. Not encrypting everything.
Comment by chanux — October 21, 2009 @ 11:10 pm
Vembu Home http://home.vembu.com, provides an alternative to DropBox:
1. You have the option of setting your own encryption password.
2. You also have the option of backing up to your local disks. You can backup online (to Amazon S3) or you can backup to your own disks locally. The choice is yours.
3. You don’t have to move your files to a particular folder to back them up.
4. Provides a web interface (and a soon to be released mobile interface) to access all your backed up files.
5. Easy to use interface.
Vembu Home is currently in limited beta. You can use the invitation code BACKUPSCANBEFUN to create an account. I would be delighted if you could try it out and let me know your opinion.
Kumar,
Vembu Technologies.
Comment by Kumar — October 22, 2009 @ 12:19 am
It doesn’t support linux. This page is for linux users.
Comment by linuxuser — April 22, 2010 @ 6:39 pm
1. You have the option of setting your own encryption password.
Interesting , but not essential.
2. You also have the option of backing up to your local disks. You can backup online (to Amazon S3) or you can backup to your own disks locally. The choice is yours.
Same as Dropbox
3. You don’t have to move your files to a particular folder to back them up.
Same as DropBox
4. Provides a web interface (and a soon to be released mobile interface) to access all your backed up files.
Same as DropBox
5. Easy to use interface.
Same as DropBox
What is the Storage limit? I am at 50GB with Dropbox for about $10/month.
Comment by TheGooch — December 17, 2010 @ 11:41 pm
Concerning automatic mounts of EncFS folders, I wrote a blog post which describes how to use Gnome’s keyring manager to auto-mount EncFS folders with stronger passwords than local user account passwords: http://obensonne.bitbucket.org/blog/20100130-encfs-keyring.html. IMHO the disadvantage of pam-mount for that task is that it uses your account passwords for EncFS encryption. Local account passwords mostly are too weak for encrypting non-local data. The mentioned post describes how to use a strong EncFS password while still automatically mounting the EncFS folder without the need to enter that crazy long password.
Oben
Comment by Oben Sonne — January 30, 2010 @ 6:22 am
Okay, this all works GREAT on paper. But what do I do to RECOVER my data when the inevitable time comes when I fry my laptop once again (by messing with settings, upgrading to Ubuntu 10.04, etc.) and when I need to re-install Ubuntu?
What do I need to back up NOW so that I can access and decrypt and access the encrypted Dropbox data when I reinstall the system?
Comment by DecryptorQuestion — April 22, 2010 @ 7:07 pm
Once you get Dropbox installed on your new system, it should synchronize all of your files onto your hard drive. The only problem is that they will all be encrypted files. You then need to install some other software, using the “sudo apt-get” and “sudo adduser” commands in section 4. Once that’s done, you can use the “encfs” command on the command-line to manually mount your encrypted directory. If you wish, you can then go on to section 5 and get it to manually mount when you log in. I have done this on several computers and it does work.
Comment by bnsmith — April 22, 2010 @ 8:22 pm
It would be nice if you added a section describing this because, besides automatic backup, it is the second use case for Dropbox: accessing your files from another computer. Once such procedure is available, even newbies would be able to make the shift.
Thank you for your howto.
Comment by Lele — January 19, 2012 @ 5:39 pm
setting it up right now. Great work! Thanks
Comment by jo — August 17, 2010 @ 7:53 am
If you change you operating System password you need to change the password on you encrypted file system also.
User this command:
encfsctl passwd ~/Dropbox
Comment by Nuno Justo — August 23, 2010 @ 5:57 am
fyi, you left out the fact tahat you have to install “libpam-mount” in your guide, took me quite a whiel to figure that out… otherwise, great guide!
Comment by eric — September 23, 2010 @ 2:07 am
my mistake, you actually did include it at an earlier step =)
Comment by eric — September 23, 2010 @ 2:07 am
Regarding my post about changing passwords (comment #20).
First you need to mount your crypt folder with
encfs ~/.dropbox_encrypted/Dropbox/encrypted ~/Dropbox
It will ask your passwords, which is the old one.
Then you change the crypt password and put the same new password as you have the linux system login with this command
encfs ~/.dropbox_encrypted/Dropbox/encrypted ~/Dropbox
And it should work flawless
Comment by Nuno Justo — November 9, 2010 @ 8:00 am
lol… the correct command to change password is this
encfsctl passwd ~/.dropbox_encrypted/Dropbox/encrypted
Comment by Nuno Justo — March 9, 2011 @ 7:57 am
Hi,
this looks really great and I am excited to try it out! But I have one question: Is it possible to encrypt only a subdirectory of the Dropbox folder such that I also have an unencrypted part that I can share with friends?
Comment by bunteKnete — April 20, 2011 @ 9:48 am
Thanks for this – works an absolute treat 🙂 Now have it working between Mac OS X, Linux(Ubuntu 10.10) and Windows 7 😀
Comment by Big F — May 4, 2011 @ 5:02 pm
Perfect, everything’s OK 😀
great work!
Comment by marinz — June 5, 2011 @ 10:49 am
For everyone who wants access on the go and is proud owner of an iPhone : there is a tool called BoxProtect which is compatible with encfs ( settings listed on http://www.boxprotect.com ).
There is version for the Mac, too (free).
Comment by nina — December 18, 2011 @ 4:45 pm